
University of Virginia

|
Department of Computer
Science University of Virginia
Defining Safety Policies |
David Evans and Andrew Twyman. Policy-Directed Code Safety. 1999 IEEE Symposium on Security and Privacy, Oakland, California, May 9-12, 1999.
.
Instead, we could write wrapper functions that perform the necessary checks and then call the original system function. To enforce the policy, we would modify the target program to call the wrapper functions instead of calling the protected system calls directly. Though wrappers are a reasonable implementation technique, they are not appropriate for describing safety policies since creating or understanding them requires intimate knowledge of the underlying system. To implement the write limit policy, the author of the safety policy would need to identify and understand every system function that may write to a file - for even a simple platform like the Java API, this involves knowing about more than a dozen different methods. Changing the safety policy would require editing the wrappers, and there would be no way to reuse a safety policy across multiple platforms.
Our solution is to express safety policies at a more abstract level and to provide a tool that generates the appropriate wrappers to enforce a safety policy on a particular platform. We express safety policies as constraints on resources and characterize system calls by how they affect those resources.
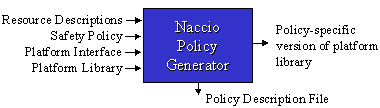
The inputs to the policy generator are the following:
The policy generator produces a policy description file that contains transformation rules required to enforce the policy. The application transformer reads these rules and transforms the application. For most policies, the policy description file contains a single rule that instructs the application transformer to rename platform library classes to use a policy-specific platform library. The other responsibility of the application transformer is to ensure the low-level code safety properties necessary to prevent the application from circumventing the high-level mechanisms. Standard techniques for low-level code safety such as bytecode verification or software fault isolation can be used effectively here.
Naccio Home Page
University of Virginia, Computer Science